How to secure Slack with low-code automation


Ben Ray
Enterprise Architect
Here's how to improve your Slack security with an easy-to-use automation template.
The rise of Slack (and potential Slack security issues)
Slack has quickly become one of the largest “Searchable Logs of All Communication and Knowledge” for hundreds of thousands of organizations. (If you didn’t know, Slack is actually an acronym, according to its CEO. I know, it blew my mind too!) In this blog, we’ll cover how to secure Slack with the Tray Platform using automation you can build yourself. (You can find a pre-built version of the workflow we’ll cover in our template library.)
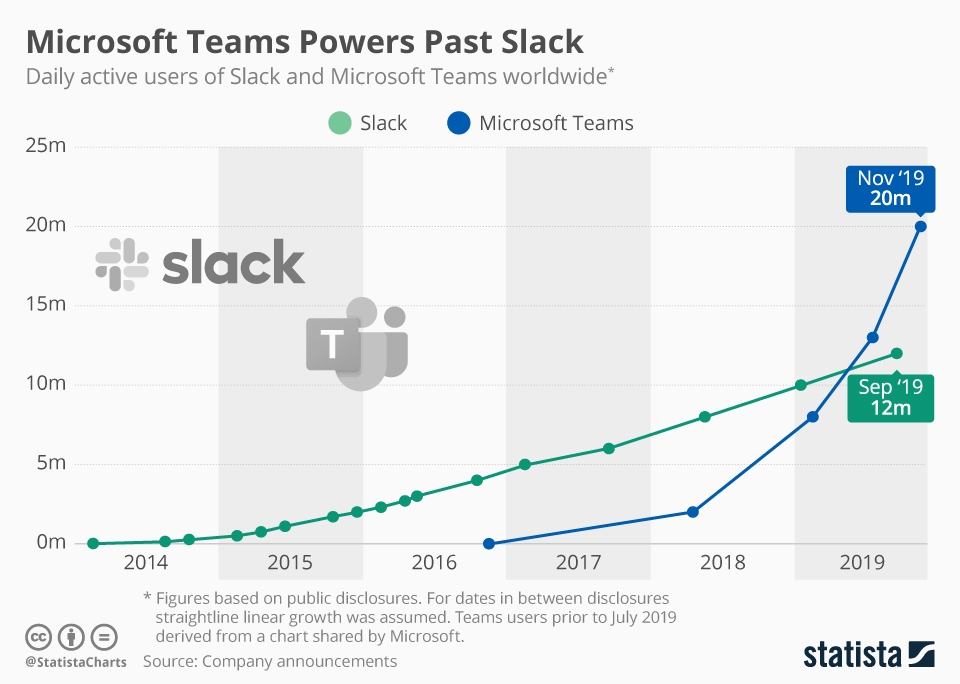
Millions of people use instant messaging every day. Image courtesy Statista. While companies used to rely heavily on email, estimates suggest that popular messaging tools such as Slack and Microsoft Teams have seen enormous adoption in recent years, exceeding more than 20 million users in total. So while messaging is becoming increasingly popular, are Slack messages secure? Actually, beyond any Slack app security issues, the rapid increase in usage, and the informality of instant messaging may be leading to increasingly frequent instances of team members accidentally oversharing sensitive information. Let’s look at a few hypothetical examples: Sharing login credentials
An employee is trying to log in to a new application and messages their team member for a username and password. The team member sends the username and password directly through a Slack message.
Sharing API tokens
Due to the “SaaS explosion,” companies are using an unprecedented number of cloud software applications. As a result, organizations are also using an unprecedented number of APIs. When using APIs, you typically need authorizations (or “auths”). Let’s say an employee needs to integrate a new app into their organization’s tech stack, so they have a team member share over an API access token. The team member takes advantage of how fast and easy it is to share things in Slack and just copy-pastes the access token in plain text format and sends it over through a direct message (or even worse, through a shared channel).
HR information
As an organization hires and onboards new team members, colleagues may share their personal information through Slack with other employees or their HR teams. They might even share their contact information, location, or social security information.
Credit card info
It’s common for organizations to purchase new software and hardware products. Employees may end up using Slack to send a company credit card number to other team members to expedite a purchase.
What do all of the above examples have in common? They all involve potentially sensitive information that team members probably shouldn’t share over Slack. If your team members’ private information gets into the wrong hands, you risk compromised security, loss of customer data, or even significant financial loss from fraudulent transactions.
Basic Slack security best practices would dictate that your teams should not use Slack to share casually:
Login credentials
API tokens
Personal information
Credit card info
It turns out there’s more you can do to ensure your teams aren’t accidentally sharing sensitive information over Slack. Let’s go over how you can use low-code automation to improve your Slack security.
How to secure Slack with automation
To ensure your team members aren’t accidentally sharing sensitive information over Slack, you could theoretically have your IT department monitor every single message across public and private channels. However, monitoring every single channel in your company is far too big and time-consuming a job for anyone. It’s also entirely possible that team members who manually watch Slack channels might accidentally miss something.
Instead, we’re going to cover how you can use low-code automation to improve your Slack security and even alert your IT department automatically whenever sensitive information pops up. At Tray.io, our security team successfully uses an automated workflow to detect and prevent data loss incidents.
Here’s a quick summary of what we’re looking to accomplish with our workflow:
We use the Tray Platform, which lets anyone build their own custom automation to send every Slack message to an automated workflow on our platform.
Within our workflow, we have a set of security keywords to look for in every message, such as “token,” “password,” “username,” or “API key.”
If our workflow detects one or more of those keywords, it alerts the security team with a link to the message so they can triage the issue at the source.
If we prefer, we can customize our list of keywords based on whichever search phrases we want our workflow to scan.
When our workflow detects a keyword on our list, it sends a Slack message to a specific channel for the security team to monitor. Here’s what the alert in our workflow looks like, but you can customize your own as needed:

Setting up our Slack security workflow
This workflow on the Tray Platform monitors a list of keywords across all Slack messages that users send. Our workflow will use our Slack connector and some of our platform’s custom data helpers such as the text helper to format keywords, and custom logic operators such as the “true/false” Boolean condition to confirm any detected keywords.
As mentioned, our workflow automatically detects any specific keywords we wish to monitor and immediately alerts our security team. Our security team can then follow up with the user(s) who shared the information and triage as needed, including:
Informing the user(s) of the correct way to share such information in the future
Delete the sensitive data as needed
Securing any at-risk systems by resetting any authentication or password details as required.
Please note: Security teams will likely consider what we’re working on to be a “high-risk workflow” since it ingests Slack messages and writes them to a dedicated Slack channel. We highly recommend setting up a dedicated Tray Platform workspace specifically to house the workflow so that only authorized builders can access it and whichever authentications might be involved.
Step 1: Import the workflow from a template
The good news is that if you’re interested in building a Slack security workflow, you don’t have to start from scratch. You can get started using this pre-built Slack security template workflow and import it directly into your instance of the Tray Platform.
Step 2: Connect your Slack account to the trigger
Within the Tray Platform, open the Slack trigger and open the authentication section. You can then set up a Slack authentication with an administrator of your Slack account–an important step that ensures the Slack trigger can capture all the messages sent within your Slack organization.
Step 3: Configure the matching keywords script
Open up the “check for matching keywords” step and edit the list of keywords to add or remove any keywords you wish to identify within Slack messages. Terms to consider adding to your Slack security list might include “token, “auth,” “password,” or “CVV.”
Step 4: Set up a Slack channel to send alerts
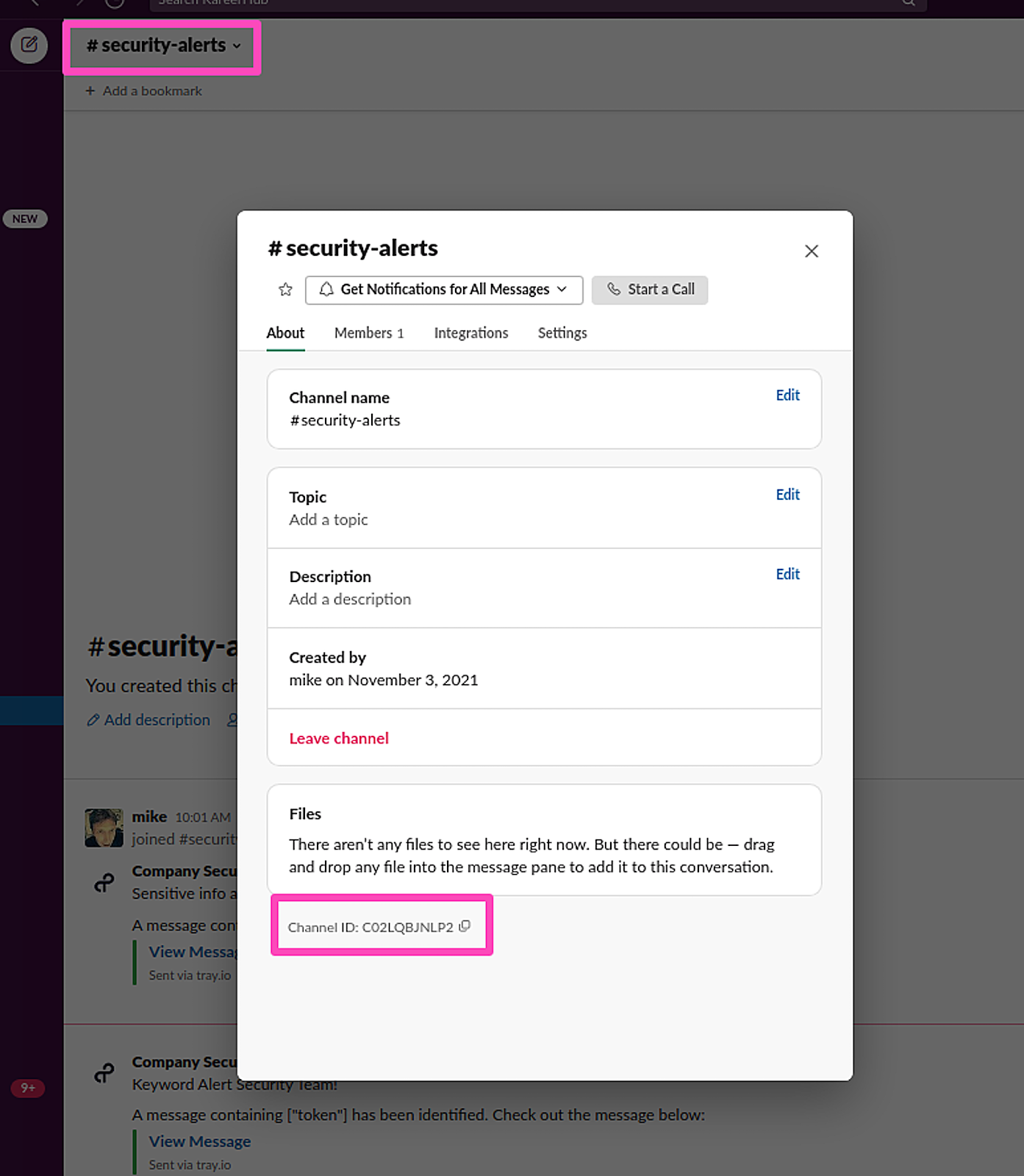
Once our workflow identifies a potential Slack security risk via keyword, we’ll want it to notify the appropriate parties to determine whether there’s an issue. Find the Slack channel ID by first creating a channel (if you don’t have one) or selecting the existing channel. (In our case, we’ll use the existing channel, “#security-alerts.”) You should see the channel ID at the bottom:
Step 5: Add a new condition to the Boolean operator
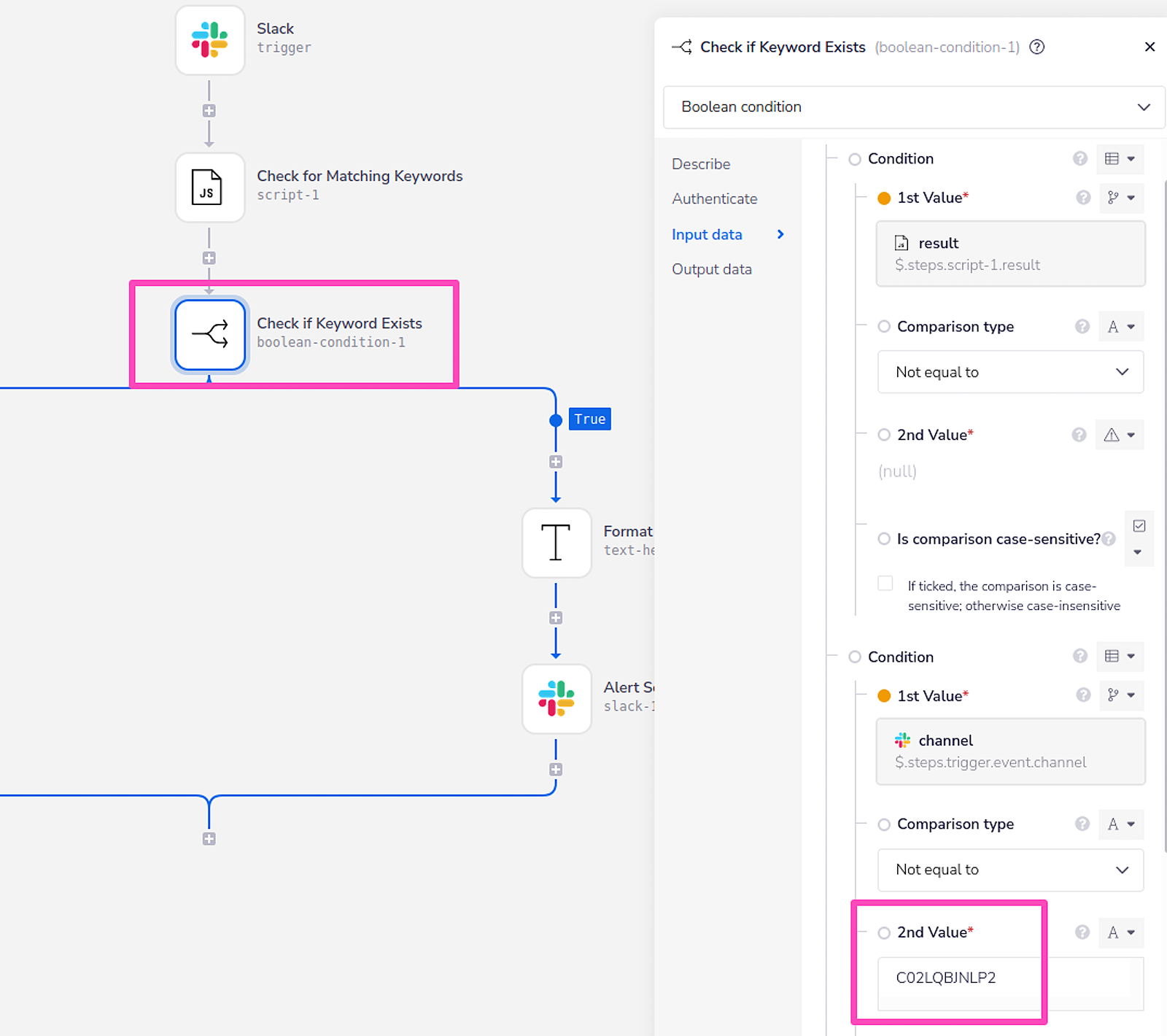
We use our Boolean to confirm any detected keywords and ensure that our workflow ignores anything it had previously sent to the #security-alerts channel we configured earlier. We can add our Slack security channel into our workflow by copying the channel ID and adding the ID as a condition into the Boolean operator as outlined in the below screenshot:
Step 6: Configure the alert message
Format the message URL to the URL of your Slack domain. We’ll also want to open up the “Alert security team” on the Slack step of our workflow template and customize how we want the message to appear.
Step 7: Enable the workflow and monitor your Slack organization
At the bottom of the workflow screen, click “enable.” Now your workflow will begin watching all Slack channels for the keywords you’ve configured.
Workflow complete!
That’s it! It’s pretty amazing that something that seems so simple can improve your Slack security so much and give your IT and security teams some much-needed peace of mind. No need to hire outside resources to monitor Slack or manually read through internal Slack logs.
Looking for more easy-to-implement workflows for your organization? Browse our template library, which we regularly update with new, pre-built templates that are ready to go. Find even more automation inspiration and learn how to automate even more use cases by joining our bi-weekly platform demo.